CVE-2023-24815: Vert.x-Web Path Traversal Escape
Introduction
A vulnerability discovered in Vert.x-Web known as CVE-2023-24815, a threat actor can exploit this vulnerability to escape the path filter leading to exfiltrate any class path resource or Path Traversal, When tunning on windows.
CVE Information
CVE-ID: CVE-2023-24815NVD Published Date: 02/09/2023NVD Last Modified: 02/17/2023CVSS 3.x: 5.3 MEDIUMCWE-ID: Improper Limitation of a Pathname to a Restricted Directory (Path Traversal)
Testing Lab
We would need an IDE in trhis case i am using IntelliJ and we would need any version of the Vert.x-Web before 4.3.8. You can download the JAR library for it from here.
What is Vert.x-Web ?
Vert.x-Web is a toolkit for building web applications and APIs using the Vert.x framework which is a polyglot, reactive, and high performance application platform for the Java Virtual Machine (JVM). It allows developers to write applications by providing a set of building blocks for creating it which include routing, authentication, authorization, templating, and serving static files. With its modular and lightweight design, Vert.x-Web enables developers to build scalable, high-performance web applications and APIs quickly and efficiently. Features of Vert.x-Web include:
Flexible routing: Define and match routes based on request methods, paths, headers, and more. You can also add request handlers, failure handlers, and response handlers to routes.Authentication and authorization: Support for a variety of authentication and authorization mechanisms, includingOAuth2,JWT,Basic, andDigestauthentication.Static file handling: Serve static files from the file system or classpath resources.WebSockets and Server-Sent Events: Support for real-time communication between clients and the server using WebSockets and Server-Sent Events.CORS and CSRF: Built-in support for Cross-Origin Resource Sharing (CORS) and Cross-Site Request Forgery (CSRF) protection.Templating engines: Support for multiple templating engines, such as Handlebars, Jade, and Thymeleaf.
The Analaysis
The vulnerability in Vert.x-Web applications running on Windows operating systems when using the StaticHandler with a wildcard mount point (*) is caused by insufficient input validation and improper handling of backslashes in user input, When request is made to the application with a crafted path the Utils.java code computes the relative path to locate the resource using the wildcard mount point, Here is example for the code:
import io.vertx.core.Vertx;
import io.vertx.ext.web.Router;
import io.vertx.ext.web.handler.StaticHandler;
public class Main {
public static void main(String[] args) {
Vertx vertx = Vertx.vertx();
Router router = Router.router(vertx);
// Configure the StaticHandler with a wildcard mount point
router.route("/*").handler(StaticHandler.create());
vertx.createHttpServer().requestHandler(router).listen(8080);
}
}
This will setup up a simple HTTP server and configure it to handle incoming requests using the Router and start listening on port 8080.
Now, Let’s take a look at the vulnerable code to analyze it and understand how the app handle the path. Here is the path for the class (vertx-web/src/main/java/io/vertx/ext/web/impl/Utils.java). The Utils.java Class contains a lot of function and the class contains various utility methods used internally by Vert.x-Web for handling requests, responses, and other web-related tasks and some of the utility methods in the Utils.java class include:
Parsing and normalizing paths: The class has methods for normalizing paths and removing redundant path elements (e.g.,./and../).Handling MIME types: There are methods for getting MIME types based on file extensions and determining the most suitable content type based on the “Accept” header in HTTP requests.Handling URL encoding and decoding: Utility methods for URL encoding and decoding of strings.Parsing and handling cookies: Methods for parsing cookies from request headers and creating Set-Cookie headers for responses.
Now, when we scroll down through the class we can see the following method pathOffset.
public static String pathOffset(String path, RoutingContext context) {
First is the define of the pathOffset method and it takes a String representing the path and a RoutingContext as arguments.
final Route route = context.currentRoute();
Here it’s getting the current Route from the RoutingContext.
if (route == null) {
return path;
} if (!route.isExactPath()) {
final String rest = context.pathParam("*");
if (rest != null) {
if (rest.length() > 0) {
if (rest.charAt(0) == '/') {
return rest;
} else {
return "/" + rest;
}
} else {
return "/";
}
}
}
In this condition If there’s no current route will return the original path, If not null it will check if the current route is not an exact path match, if yes Retrieve the wildcard path parameter (denoted by *) and then check if the wildcard path parameter exists. If the wildcard path parameter exists it will normalize the wildcard path parameter by ensuring it starts with a forward slash (/) and return it. If the parameter is empty it return a single forward slash. And here where is the problem occures.
Patch Diffing
The patch for this vulnerability done as the following(We can find the commit here):
First it’s added the following lines to the Utils.java class:
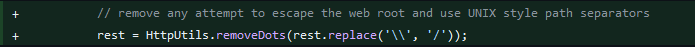 And the doal of adding this lines is to remove the backslashes
And the doal of adding this lines is to remove the backslashes \ with the forwardslashes /. Second they added new class called StaticHandlerWindowsTest and te purpose of this class is to test the behavior of the StaticHandler class on Windows operating systems. This is done by testing the ability of the StaticHandler class to prevent path traversal attacks by attempting to escape to the classpath from different types of routes. Class Code:
package io.vertx.ext.web.handler;
import io.vertx.core.http.HttpMethod;
import io.vertx.ext.web.WebTestBase;
import org.junit.Test;
public class StaticHandlerWindowsTest extends WebTestBase {
@Test
public void testEscapeToClasspathFromWildcard() throws Exception {
router.clear();
router.route("/*").handler(StaticHandler.create("www"));
// attempt to escape to classpath, given that the handler is mounted on a wildcard,
// reading the wildcard must return a sanitized path and therefore not allow to escape.
testRequest(HttpMethod.GET, "/..\\.htdigest", 404, "Not Found");
}
@Test
public void testEscapeToClasspathFromNull() throws Exception {
router.clear();
router.route().handler(StaticHandler.create("www"));
// attempt to escape to classpath, given that the handler is mounted on a catch all path
testRequest(HttpMethod.GET, "/..\\.htdigest", 404, "Not Found");
}
@Test
public void testEscapeToClasspathFromRegEx() throws Exception {
router.clear();
router.routeWithRegex(".*").handler(StaticHandler.create("www"));
// attempt to escape to classpath, given that the handler is mounted on a regex,
testRequest(HttpMethod.GET, "/..\\.htdigest", 404, "Not Found");
}
@Test
public void testEscapeToClasspathFromFixedPath() throws Exception {
router.clear();
router.routeWithRegex("/").handler(StaticHandler.create("www"));
// attempt to escape to classpath, given that the handler is mounted on a regex,
testRequest(HttpMethod.GET, "/..\\.htdigest", 404, "Not Found");
}
}
Conclusion
Finally, We highlighted the issue and the mistake behind it & explained the vulnerable code by analyzing and going through it, Also, We discuss the the patch and how the vulnerability got patched in a simple way. To protect yourself from this vulnerability simply upgrade to the last version
References
- https://vertx.io/docs/vertx-web/java/
- https://github.com/vert-x3/vertx-web/blob/62c0d66fa1c179ae6a4d57344631679a2b97e60f/vertx-web/src/main/java/io/vertx/ext/web/impl/Utils.java#L83
- https://github.com/vert-x3/vertx-web/commit/9e3a783b1d1a731055e9049078b1b1494ece9c15
- https://github.com/vert-x3/vertx-web
- https://jar-download.com/artifacts/io.vertx/vertx-web