Homograph Attack: Abusing IDNs for Phishing
Introduction
In recent years, phishing and social engineering attacks have become a significant threat to businesses and individuals alike. These attacks are particularly dangerous because they target end-users directly, bypassing many traditional cyber security defenses such as firewalls, endpoint detection and response (EDR), and anti-virus software. To combat these threats, many companies have implemented phishing awareness training programs to educate employees on how to spot suspicious email attempts and protect themselves and the business from bad actors. However, even with user awareness, it can be difficult to limit or prevent certain types of attacks, such as homograph attacks, where the attacker uses seemingly legitimate websites or emails to trick the user.
What is phishing ?
Phishing is a type of social engineering attacks that uses deception to trick individuals into providing sensitive information such as login credentials or personal data. This type of attack typically occurs through email, telephone, or text message communication and is designed to appear legitimate in order to gain the trust of the victim. The attackers may use various tactics such as creating fake websites or emails that resemble legitimate sources, impersonating a trusted organization, or using urgent language to create a sense of urgency and pressure the victim into providing the requested information. The goal of these attacks is to steal sensitive information such as passwords, credit card numbers, or other personal data for financial gain or to gain access to sensitive systems and information.
Types of Phishing
Email Phishing
Email Phishing is a tactic used in penetration testing and red teaming engagements where an attacker targets a specific company or individual by gathering information through Open-source intelligence (OSINT). This type of attack involves researching the company, their interests, and the services they offer in order to appear legitimate and trick the target into taking a desired action. An example of this type of attack is Spear Phishing, where the attacker poses as someone searching for a job and targets the human resources department of the company. The attacker then tricks the HR representative into downloading a malicious file, such as a keylogger or spyware, which allows the attacker to gain access to sensitive information. The goal of Email Phishing is to gather information or gain access to a company’s systems through tricking the target into taking an action that they would not normally take.
Whaling Phishing
Whaling phishing is a specific type of phishing that targets individuals with high levels of access and permissions within an organization, such as the CEO. This tactic involves creating fake emails that appear to be from other individuals within the company, in order to gain sensitive information or access to important systems. The goal of whaling phishing is to take advantage of the trust and authority of high-level individuals in order to compromise the entire organization. To carry out a successful whaling phishing attack, an attacker may conduct extensive research on the targeted organization, known as OSINT (Open Source Intelligence). This research may include studying the roles, positions, and groups within the company, in order to identify potential targets and understand their access levels. Once the attacker has a good understanding of the organization, they may create fake emails that appear to be from other individuals within the company. These emails may contain malicious links or attachments, which, when clicked, can infect the target’s computer with malware or steal sensitive information. For example, imagine that the CEO of a company has local administrator access on the company’s system. An attacker may create a fake email that appears to be from a lower-level employee, requesting the CEO to click on a link or download a file. If the CEO falls for the trap and clicks on the link or download the file, the attacker can potentially gain access to the CEO’s computer and potentially the entire company’s system. In summary, whaling phishing is a tactic that targets high-level individuals within an organization, such as the CEO, with the goal of compromising the entire organization. It involves conducting extensive research on the targeted organization and creating fake emails that appear to be from other individuals within the company, in order to steal sensitive information or gain access to important systems.
Smishing Phishing
Smishing, also known as SMS phishing, is where the attacker sends text messages to the victim in order to obtain sensitive information or trick them into taking a specific action. Unlike traditional phishing attacks, which are delivered through email, smishing attacks are delivered through text messages on a victim’s mobile device. The attacker may obtain the victim’s phone number through an old data breach or other means, making it easy for them to target the victim. One of the advantages of smishing is that it does not require an internet connection. This means that even if the victim is on vacation or in an area with limited internet access, they can still be targeted by the attacker. Additionally, the victim may be more likely to respond to a text message than an email, as text messages are typically considered more urgent and personal. However, it is important to note that smishing can be just as dangerous as traditional phishing attacks. The victim may be tricked into providing sensitive information, such as login credentials or financial information, or they may be directed to a malicious website that can infect their device with malware. Therefore, it is important for individuals and organizations to be aware of the risks of smishing and to take appropriate measures to protect themselves.
Vishing Phishing
Vishing, also known as voice call phishing, is where the threat actor contacts the victim or targeted person via phone call. The attacker may use phone numbers over IP (Internet Protocol) if they have already gained access to them. This method of phishing is considered harder compared to others, as the attacker must have a well-planned and convincing story in order to obtain the desired information from the victim without arousing suspicion. One benefit of vishing is that the outcome of the attack is often faster than email phishing, as the attacker does not need to wait for a file or email to be opened or clicked. It is important to note that there is often confusion between phishing and spear phishing. The main difference between the two is that spear phishing targets specific groups or organizations, such as individuals with specific positions that have access to sensitive systems.
What is IDN’s ?
International Domain Names (IDNs) are a solution to the problem of the limited character set of the early days of the World Wide Web’s Domain Name System (DNS). The DNS root originally only supported Latin letters A-z and digits. However, with over 6000 languages spoken worldwide, it became clear that support for non-Latin alphabets such as Cyrillic and Arabic was necessary. IDNs were created to address this issue and make the DNS root more inclusive and accessible for speakers of non-Latin languages. Additionally, IDNs also play a significant role in Homograph attacks, that uses visually similar characters to trick users into visiting malicious websites.
IDN Homograph Attack
An IDN Homograph Attack is an attack that utilizes the Internationalized Domain Name (IDN) feature to manipulate letters in different languages. The IDN feature allows for the use of non-Latin characters in domain names, which can be used to create a spoofed version of a legitimate domain that looks very similar to the original. This can be used to trick victims into providing sensitive information, such as login credentials or personal information, through phishing emails or other means. In a demonstration of an IDN Homograph Attack, an attacker may use a tool such as the Homoglyph Attack Generator (https://www.irongeek.com/homoglyph-attack-generator.php) to create a spoofed version of a trusted domain. For example, the attacker may create a domain that looks like “hackerone.com” but uses non- Latin characters that are visually similar to the letters “h”, “a”, “c”, “k”, “e”, “r”, “o”, “n” and “e”. The victim may not realize that the domain is different from the legitimate “hackerone.com” and may enter their login credentials or personal information, allowing the attacker to steal their information.
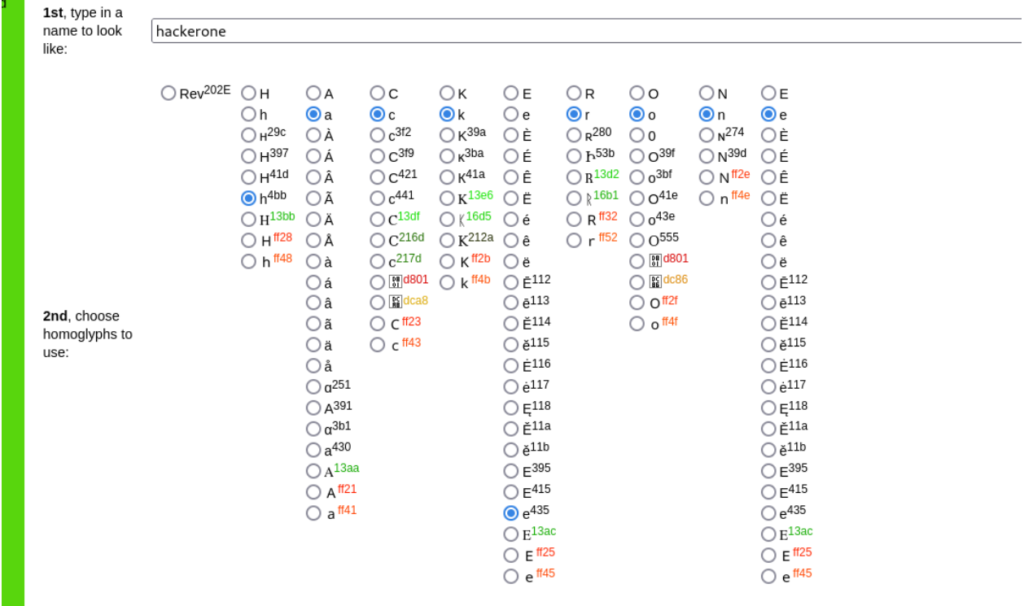
As you can observe in the picture, we utilized characters from a different language, specifically “cyrillic” letters, to create a domain name that appears similar to “hackerone.com”. However, it is important to note that the domain name in question, һackеrone.com, is not the same as the legitimate domain “hackerone.com”.
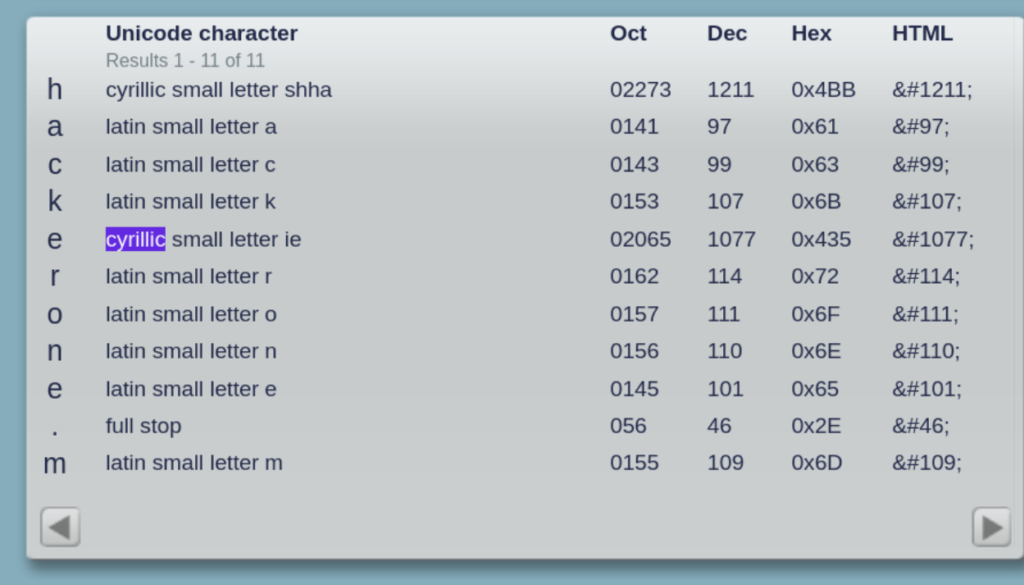
And here is the domain available as we can see:
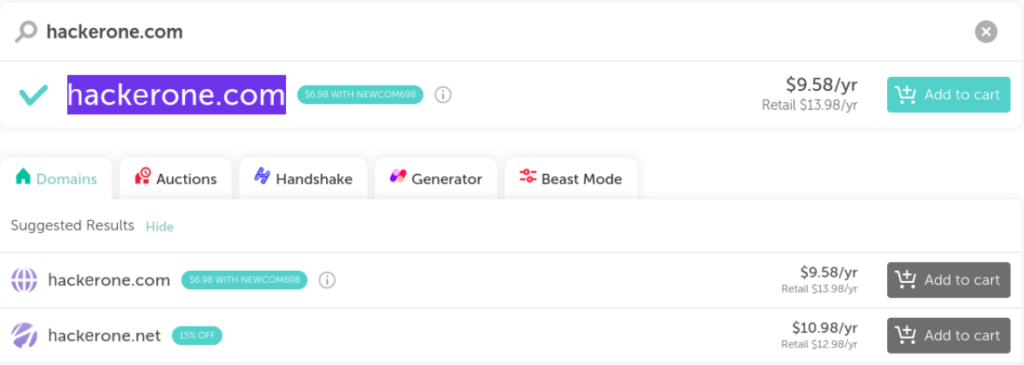
By using the domain support@hackerone.com as the original domain, in order to steal their HackerOne account. This is a simple simulation of this type of attack and it can be used in different scenarios, depending on the target. This attack is specifically found in common browsers like Google Chrome, specifically in version 58 and Chromium-based browsers, but it also exists in Firefox. However, we will cover how to limit the risk of this attack in Firefox as well.
What is punycode ?
Punycode is a method of encoding Unicode characters in the ASCII character set. Unicode is a standardized system of representing characters and symbols from different languages and scripts, while ASCII is a standardized set of characters and symbols used in computer systems. Punycode allows the use of Unicode characters in domain names and URLs, which are typically limited to the ASCII character set. The process of converting Unicode characters to Punycode involves a series of steps. First, the Unicode characters are divided into basic and non-basic characters. Basic characters are those that are already included in the ASCII character set, while non-basic characters are those that are not. Next, the non-basic characters are assigned a unique code point, which is a numerical value that represents the character. The code point is then converted to a series of ASCII characters using a specific algorithm. These ASCII characters are then prepended with the prefix xn– , which indicates that the characters following it are Punycode encoded. When a user enters a Punycode encoded URL, the browser will convert the Punycode back to Unicode characters and display the correct characters on the screen. An example of Punycode in action is the domain name xn– d1acufc.xn–p1ai , which is the Punycode version of the Russian domain name рф.рф (rf.rf) . In this example, the non-ASCII characters р and ф have been encoded in Punycode, allowing them to be used in the domain name. In summary, Punycode is a method of encoding Unicode characters, which are used in different languages and scripts, into the ASCII character set, which is widely used in computer systems. This allows the use of Unicode characters in domain names and URLs, which would otherwise not be possible.
Limit the attack
In order to limit the risk of attack in Firefox browser, there are a few steps you can take. First, open your Firefox browser and type about:config in the address bar and enable it:
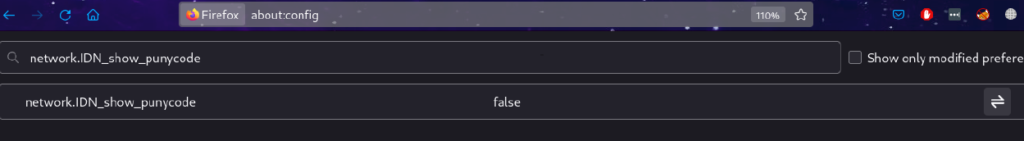
The attack fixed in some common used browsers, but it’s still exist in firefox. We will cover blow how to limit the risk of this attack in firefox & Goolge.
Prevent and Detect homograph attack and HTTP spoofing
HTTP spoofing is an attack in which an attacker creates a fake website that looks identical to the original website. This can be done by using SSL certificates to make the fake website appear secure and trustworthy. However, it is important to pay attention to the certificate information to confirm the owner of the domain and website. To prevent and mitigate this type of attack, it is recommended to disable punycode in the address bar as most modern browsers have this feature. When punycode is disabled, the user will see the punycode as unicode, making it easier to identify suspicious websites. Additionally, using third-party tools such as virustotal can also help to check the authenticity of a website’s URL.
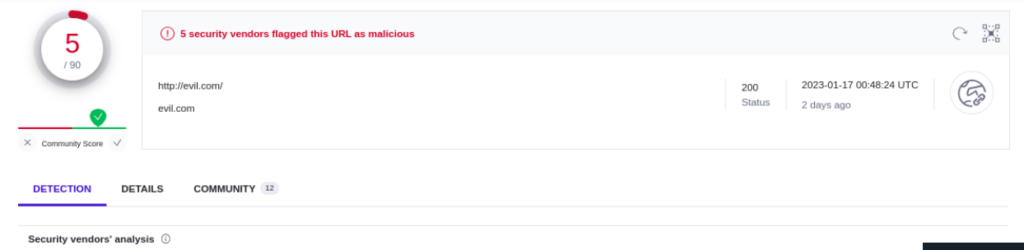
Conclusion
In conclusion, phishing and social engineering attacks are a significant threat to businesses and individuals alike. These attacks target end-users directly and bypass traditional cyber security defenses. To combat these threats, many companies have implemented phishing awareness training programs to educate employees on how to spot suspicious email attempts and protect themselves and the business from bad actors. However, even with user awareness, it can be difficult to limit or prevent certain types of attacks, such as homograph attacks. Email Phishing, Spear Phishing, and Whaling Phishing are some of the types of phishing that can be used by attackers to gain sensitive information or access to important systems. It is important for organizations and individuals to be aware of these tactics and to take necessary precautions to protect themselves and their data from phishing attacks.